Overview:
Encrypted Client Hello is a newer feature within Cloudflare and is rapidly becoming a new standard for security.
The basic concept is that the normal TLS Client Hello message towards the TLS Server is encrypted within an outer Client Hello message that references “cloudflare-ech.com”. The end result is that web filtering appliances see that URL in their logs based on the SNI of the outer Hello rather than the actual SNI they are navigating to.
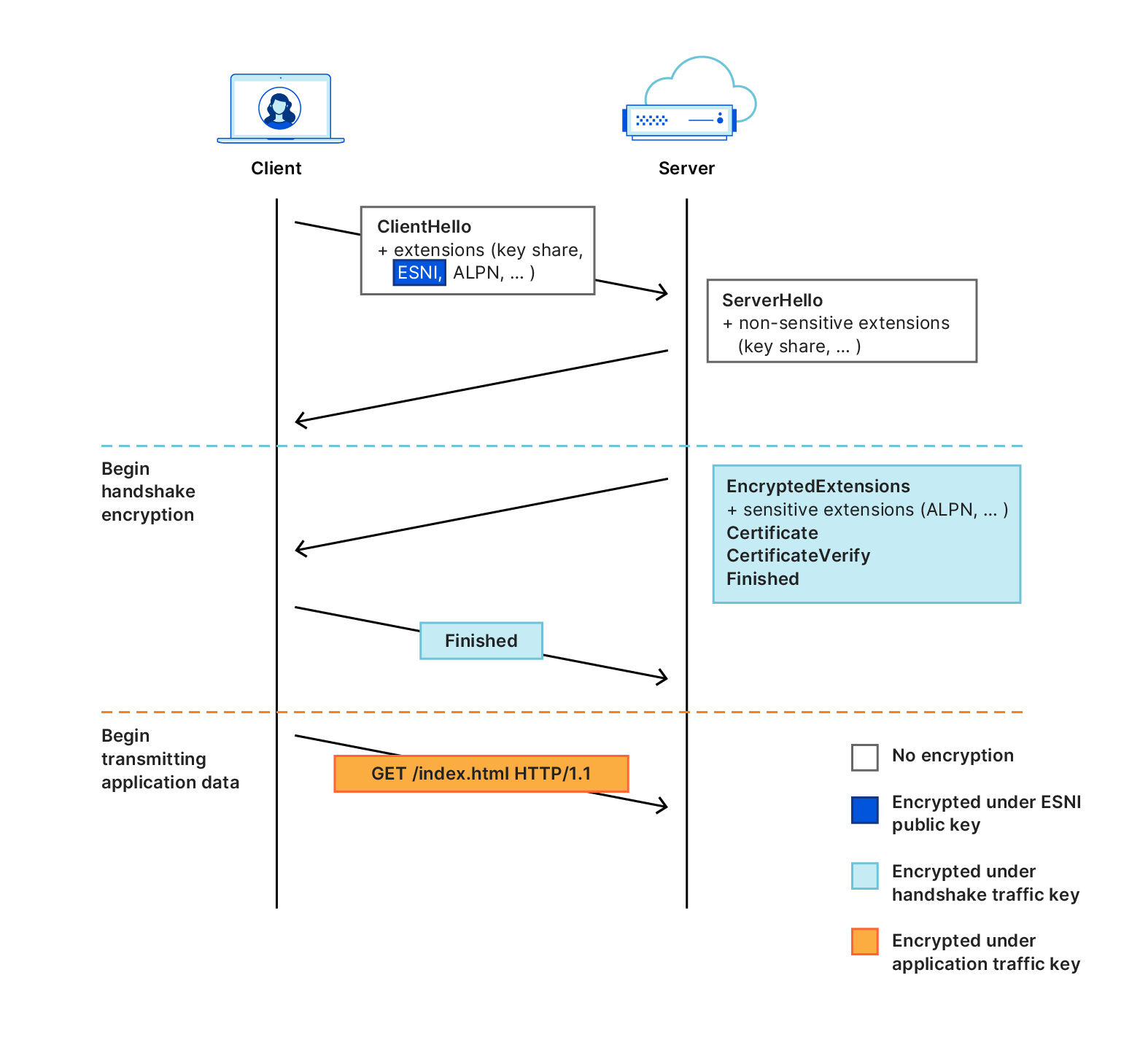
This is great for end-user privacy, but less great for Enterprise network administrators who are trying to filter Internet traffic. The challenge is that while you can of course block “cloudflare-ech.com” you may inadvertantly block legitimate sites that end users need to access.
The basic solution is to block or alter queries for use-application-dns.net. The preferred response is NXDOMAIN, but that main be challenging to achieve depending on your network architecture.
To check and see if a site is using ECH, Cloudflare has a built-in trace tool for all of their sites available at https://{{ domain }}/cdn-cgi/trace. My own site has ECH enabled and you can see the trace here: https://davissystem.net/cdn-cgi/trace - Specifically, the sni= section of the response is what you’re looking for.
Blocking:
BIND9 can be configured to respond with NXDOMAIN to specific queries using a Response Policy Zone.
Here is an example named.conf file and zone file to accomplish that task, note that this configuration does not perform recursion - it just spits out the NXDOMAIN for use-application-dns.net.
This same approach can also be used for iCloud private relay by also including mask.icloud.com and mask-h2.icloud.com within your RPZ file.
options {
max-cache-size 1024m;
max-ncache-ttl 5m;
max-cache-ttl 24h;
directory "/var/cache/bind";
pid-file "/var/run/named/named.pid";
allow-query { any; };
recursion no;
listen-on { any; };
listen-on-v6 { none; };
dnssec-validation auto;
response-policy {
zone "deny.rpz" policy nxdomain;
};
};
zone "deny.rpz" {
type master;
file "/var/cache/bind/deny.rpz";
};
Here is an example RPZ file:
$TTL 300
@ IN SOA localhost. admin.localhost. (
1 ;
2h ;
30m ;
30d ;
1h ;
)
IN NS localhost.
; The following list of IP addresses will NXDOMAIN.
use-application-dns.net CNAME .
mask.icloud.com CNAME .
mask-h2.icloud.com CNAME .